There are several other thousands of Viruses and Malwares that can infect various types of devices from mobile handhelds to Servers, leading to compromise and in some extreme cases total destruction of data. Current estimates of the actual number of Viruses and Malwares in existence vary widely. Understanding what Viruses and Malwares are can help considerably in detection and prevention of these threats.
A Virus is a form of Malware itself, it is a piece of programmed computer code that attaches itself to other computer programs, data files or boot sector of a hard drive and then replicates itself when executed, infecting other files, programs and computers without the permission or knowledge of the user. Some Viruses are designed to completely replace host files and programs. Infections can result in poor system performance, loss of data and or disk space and creating backdoors and other loopholes in the system.
The first Virus called the Creeper Virus was discovered in the early 1970s on the first running internet network ARPANET. Creeper gained access to other remote systems via ARPANET and copied itself to these systems where the message, "I'm the creeper, catch me if you can!" was displayed.
Malware is the short name for malicious software and it is used to generically describe any malicious software regardless of technical category either a Virus, Worm, Trojan, BotNet e.t.c. It is a piece of software program that is built and used to compromise or disrupt a system's normal operation, carry out various types of fraud after gathering confidential and sensitive information from compromised devices, systems or networks.
Stuxnet is one of the worlds most advanced and sophisticated Malware. It was designed specifically to target industrial operations around the world. Cybersecurity experts say that it is the first known cyber-super-weapon designed to destroy a real-world target as it is believed that Stuxnet was used to take out Iran’s nuclear reactor.
Common types of malwares include:
- Virus: As discussed above. This is mostly spread when software or storage disks are shared between computers and other devices.
- Adware: Also known as advertising supported software. After installation or infection, advertisements are presented to the users screen. Not all adware has malicious intent as some are programmed to examine which Internet sites the user visits frequently and present features related advertisements.
- Spyware: This is malicious software that spies on the user, tracks internet activities and helps the attacker gather information about the victim without the knowledge or consent of the victim. Some spywares like key loggers may be installed intentionally by an organization to monitor activities of employees
- Worm: This type of malware replicates itself on the network and systems and destroys information and files saved on the host system.
- Trojan: This is a malicious program designed to steal personal, financial information or take over the resources of a system. They are usually disguised to make a user think they are legitimate software programs.
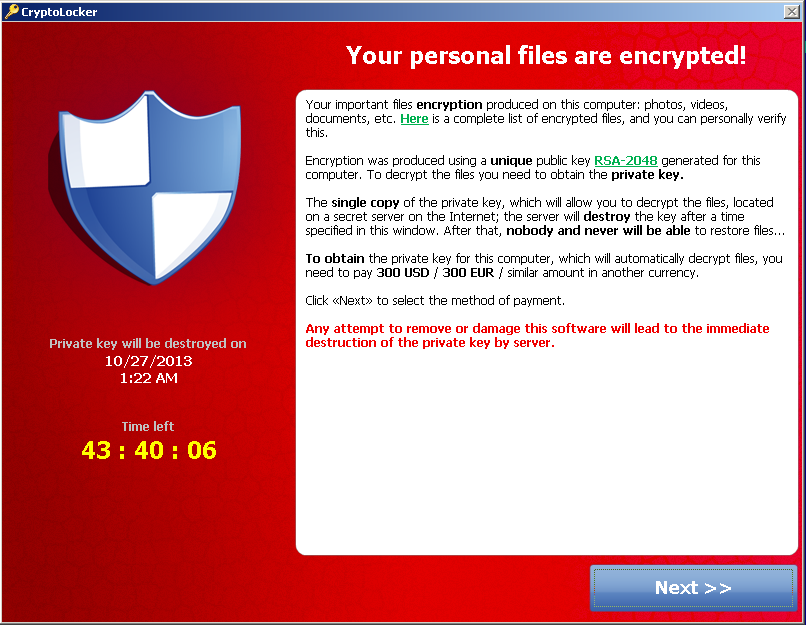
- Ransomeware: This is an advance type of malware that restricts access to a computer or resource until the author or attacker is paid a fee. An example is the aforementioned CyptoLocker ransomeware.
- Bot: This is a short term for Robot and it is used to automate tasks. Some bots can be used to allow a remote attacker control of a victim’s system. The nature of bots attacks is such that it is as easy to control one system as it is controlling hundreds of thousands of systems. Bots can be used to send spam, download and store illegal file e.g porn, or to make computers participate in attacks on other computers and networks. A bot can be made to search a Victim’s hard drive and send confidential information to a remote server on the internet in order to perform identity theft. Computers that are infected with bots are often called drones or zombies.
- Hoaxes: These are silly pranks or a form of chain mails used to generate fear, uncertainty and doubts in affected victims. Some malicious Hoaxes have made victims delete legitimate files unknowingly from their systems.
- BotNet: A botnet is a group of bot infected systems that are all controlled by the same "command and control center".
- Phishing: This is a social engineering attack that attempts to fraudulently acquire sensitive information such as passwords, banking or credit card details from users. This is usually achieved by sending e-mail or other similar communication messages masquerading as a trustworthy person or business with an apparently legitimate reason for request of information.
- Payload: This is an additional information or functionality that may be included in other forms of malware e.g data stealing, disk overwriting, BIOS flashing e.t.c
- Rootkit: is a collection of one or more tools designed to covertly maintain control of a system. When installed, a rootkit uses functions in the operating system to hide itself so as not to be detected. They are often used to hide other malicious programs such as keystroke loggers.
As a mobile or computer user, it is a frustrating and alarming experience to have your hard work held hostage or destroyed by a virus or your identity and banking details stolen and used for malicious intents. Protecting oneself from threats or Malwares is important and can be carried out using various means such as use of proactive Antiviruses, Malware scanners, rootkit removers, firewalls, intrusion detection systems and other vulnerability scanners.
Leave a Comment